Connect ZOOT NATIVE + static IP using VyOS.
ZOOT NATIVE + static IP
It is an IPoE connection service provided by InterLink. In spite of IPv4 over IPv6 technology, one static global IP address (IPv4) can be published.
Launch a new VyOS
Click here for new setup VyOS installation
It was very helpful. Qita - Use the transix ipv4 connection (static IP) on VyOS Special thanks!
My server environment
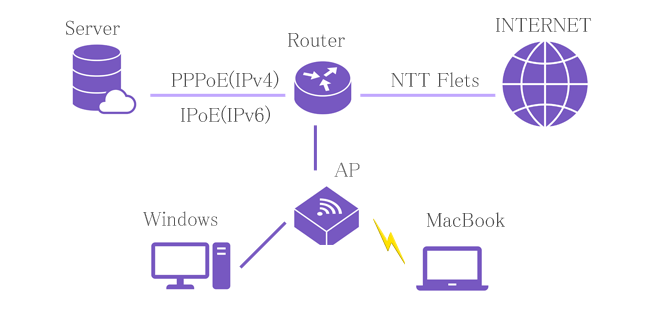
Router: NTT Flets PR-400NE (PPPoE pass through, 192.168.8.1)
│
├─ Server: Ubuntu server 22.04 (192.168.8.3 gw 192.168.8.10)
│ ├─ kvm
│ │ ├─ VyOS2(PPPoE, 192.168.8.9, Via provider) *1
│ │ └─ VyOS4(IPoE, 192.168.8.10, IPv4 over IPv6 on transix, DHCP server)
│ └─ LXD container
│ ├─ DNS2(192.168.8.7, gw 192.168.8.9) *1
│ ├─ Web2(192.168.8.74, gw 192.168.8.9) *1
│ ├─ Mail2(192.168.8.8, gw 192.168.8.9) *1
│ ├─ DNS4(192.168.8.27, gw 192.168.8.10)
│ ├─ Web4(192.168.8.75, gw 192.168.8.10)
│ └─ Mail4(192.168.8.28, gw 192.168.8.10)
│
└─ AP: 11ac Wifi
├─ Desktop PC: Windows11(192.168.8.153, gw 192.168.8.10 DHCP client)
└─ Note PC: MacBook(192.168.8.154, gw 192.168.8.11 DHCP client)
*1) Once the IPoE connection is stable, stop PPPoE.
I already use the connection service "ZOOT NEXT"(Connect PPPoE, static IPv4 x 1). Don't touch it because it can be connected stably with VyOS. Launch a new VyOS (KVM guest) for ZOOT NATIVE connection. (ZOOT NEXT and ZOOT NATIVE can be used at the same time.) Once the IPoE connection is stable, stop PPPoE.
Configure VyOS
Configure an interface.
# eth0
set interfaces ethernet eth0 address 2400:XXXX:XXXX:2100::feed/64 # Prefix + ::feed
set interfaces ethernet eth0 address 192.168.8.10/24
set interfaces ethernet eth0 dhcpv6-options parameters-only
set interfaces ethernet eth0 ipv6 address autoconf
# tun0
set interfaces tunnel tun0 address 13X.XXX.XXX.146/32 # My global IP
set interfaces tunnel tun0 encapsulation ipip6
set interfaces tunnel tun0 ip adjust-mss 1420
set interfaces tunnel tun0 mtu 1500
set interfaces tunnel tun0 remote 22XX:XXXX::feed:143 # transix IP
set interfaces tunnel tun0 source-address 24XX:XXXX:XXXX:2100::feed # eth0 IPv6
# NGN(IPv6)
# MTU = 1500 = 1518 - 14(Ethernet Header) - 4(FCS)
# ipip6
# MSS = 1420 = 1500 - 40(IPv6 Header) - 20(IPv4 Header) - 20(TCP header)
Configure protocols (static route)
set protocols static route 0.0.0.0/0 interface tun0
set protocols static route 192.168.8.0/24 interface eth0
Configure a firewall.
set firewall global-options all-ping enable
set firewall global-options broadcast-ping disable
# accept_all
set firewall ipv4 name accept_all default-action "accept"
set firewall ipv4 name accept_all rule 2 action "drop"
set firewall ipv4 name accept_all rule 2 state "invalid"
# public_to_local (WWW <=> VyOS)
set firewall ipv4 name public_to_local default-action "drop"
set firewall ipv4 name public_to_local rule 1 action "accept"
set firewall ipv4 name public_to_local rule 1 state "established"
set firewall ipv4 name public_to_local rule 1 state "related"
set firewall ipv4 name public_to_local rule 2 action "drop"
set firewall ipv4 name public_to_local rule 2 state "invalid"
set firewall ipv4 name public_to_local rule 3 action "accept"
set firewall ipv4 name public_to_local rule 3 protocol "icmp"
# public_to_private (WWW <=> DMZ)
set firewall ipv4 name public_to_private default-action "drop"
set firewall ipv4 name public_to_private rule 3 action "accept"
set firewall ipv4 name public_to_private rule 3 state "established"
set firewall ipv4 name public_to_private rule 3 state "related"
set firewall ipv4 name public_to_private rule 4 action "drop"
set firewall ipv4 name public_to_private rule 4 state "invalid"
set firewall ipv4 name public_to_private rule 80 action "accept"
set firewall ipv4 name public_to_private rule 80 description "HTTP"
set firewall ipv4 name public_to_private rule 80 destination port "80"
set firewall ipv4 name public_to_private rule 80 protocol "tcp"
# accept_all_v6 (IPv6)
set firewall ipv6 name accept_all_v6 default-action "accept"
set firewall ipv6 name accept_all_v6 rule 2 action "drop"
set firewall ipv6 name accept_all_v6 rule 2 state "invalid"
# public_to_local_v6 (WWW <=> VyOS)
set firewall ipv6 name public_to_local_v6 default-action "drop"
set firewall ipv6 name public_to_local_v6 rule 1 action "accept"
set firewall ipv6 name public_to_local_v6 rule 1 state "established"
set firewall ipv6 name public_to_local_v6 rule 1 state "related"
set firewall ipv6 name public_to_local_v6 rule 2 action "drop"
set firewall ipv6 name public_to_local_v6 rule 2 state "invalid"
set firewall ipv6 name public_to_local_v6 rule 3 action "accept"
set firewall ipv6 name public_to_local_v6 rule 3 protocol "icmpv6"
# public_to_private_v6 (WWW <=> DMZ)
set firewall ipv6 name public_to_private_v6 default-action "drop"
set firewall ipv6 name public_to_private_v6 rule 1 action "accept"
set firewall ipv6 name public_to_private_v6 rule 1 state "established"
set firewall ipv6 name public_to_private_v6 rule 1 state "related"
set firewall ipv6 name public_to_private_v6 rule 2 action "drop"
set firewall ipv6 name public_to_private_v6 rule 2 state "invalid"
Configure a firewall zone.
# local (VyOS <= DMZ, VyOS <= WWW)
set firewall zone local default-action "drop"
set firewall zone local from private firewall ipv6-name "accept_all_v6"
set firewall zone local from private firewall name "accept_all"
set firewall zone local from public firewall ipv6-name "public_to_local_v6"
set firewall zone local from public firewall name "public_to_local"
set firewall zone local local-zone
# private (DMZ <= local, DMZ <= WWW)
set firewall zone private default-action "drop"
set firewall zone private from local firewall ipv6-name "accept_all_v6"
set firewall zone private from local firewall name "accept_all"
set firewall zone private from public firewall ipv6-name "public_to_private_v6"
set firewall zone private from public firewall name "public_to_private"
set firewall zone private interface "eth0"
# public (WWW <= local, WWW <= DMZ)
set firewall zone public default-action "drop"
set firewall zone public from local firewall ipv6-name "accept_all_v6"
set firewall zone public from local firewall name "accept_all"
set firewall zone public from private firewall ipv6-name "accept_all_v6"
set firewall zone public from private firewall name "accept_all"
set firewall zone public interface "tun0"
Configure NAT(DNAT)
# WWW => HTTP
set nat destination rule 80 description HTTP
set nat destination rule 80 destination port 80
set nat destination rule 80 inbound-interface tun0
set nat destination rule 80 protocol tcp
set nat destination rule 80 translation address 192.168.8.75
Configure NAT(SNAT)
# Access to WWW
set nat source rule 20 description "eth0 => tun0"
set nat source rule 20 outbound-interface tun0
set nat source rule 20 source address 192.168.8.0/24
set nat source rule 20 translation address masquerade
Configure DHCP server
set service dhcp-server shared-network-name NTT_NETWORK subnet 192.168.8.0/24 option default-router "192.168.8.10"
set service dhcp-server shared-network-name NTT_NETWORK subnet 192.168.8.0/24 option name-server "192.168.8.10"
set service dhcp-server shared-network-name NTT_NETWORK subnet 192.168.8.0/24 range 160 start "192.168.8.160"
set service dhcp-server shared-network-name NTT_NETWORK subnet 192.168.8.0/24 range 160 stop "192.168.8.220"
set service dhcp-server shared-network-name NTT_NETWORK subnet 192.168.8.0/24 subnet-id "8"
The router and AP vassal devices are assigned IP addresses of 192.168.8.0/16 and connect to the Internet via Gateway 192.168.8.10 and then transix.